Defend your inbox by spotting these 6 telltale phishing lures
Are you able to effectively spot a phishing email? We sure hope so, especially because over 95% of successful cyber attacks today — including the big ones you hear about in the news — begin with phishing. Take a peek below and see if you can identify all of the red flags which should cause you to worry that this may not be a legitimate message.
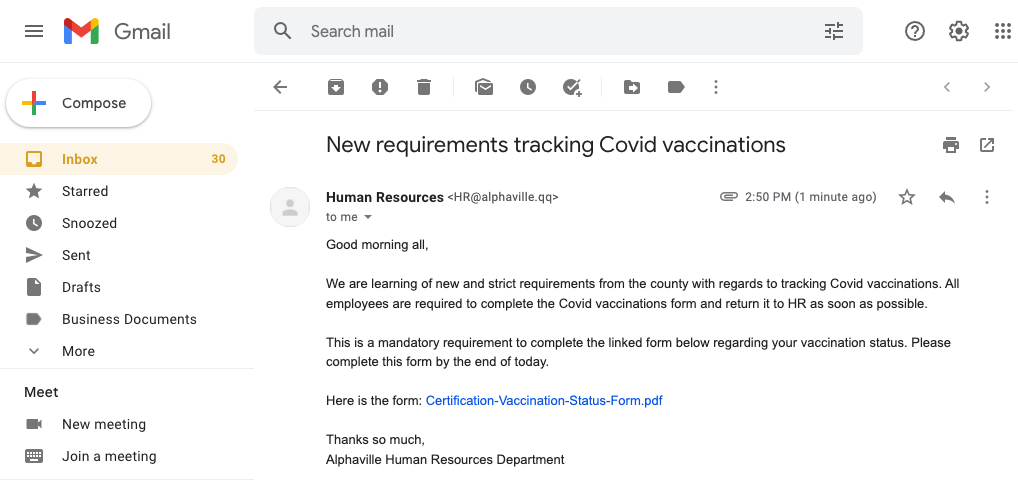
Did you catch them all?
Hopefully, you did, but even if you missed one or two you should still have been suspicious enough of this message to stop and think before you did anything else. Let’s take a look at what you should have identified.
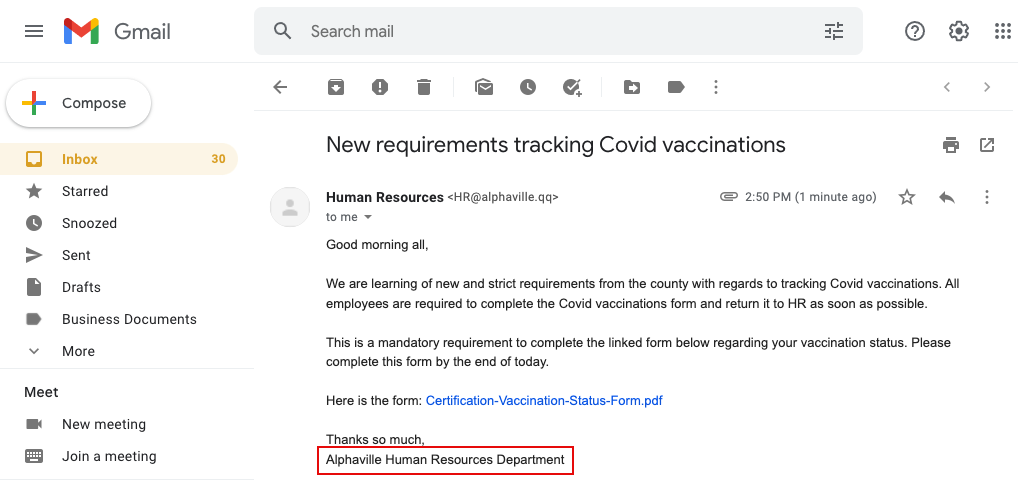
Red Flag 1: Message from an important source. Any time you receive a message from an important group, person or division, make sure that you take extra precautions. These types of senders are commonly spoofed or used during a phishing attack.
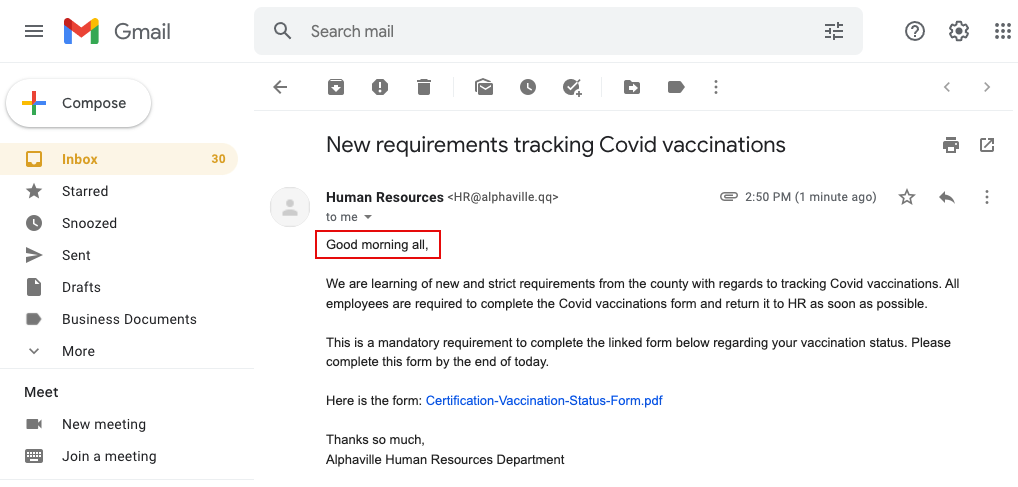
Red Flag 2: Ambiguous salutation. You should have a good feel for how your different teams and organizations write and communicate within your organization. Pay attention to the beginning of any message, as this is where an attacker will try to lure you in. Make sure it doesn’t look or sound out of place.
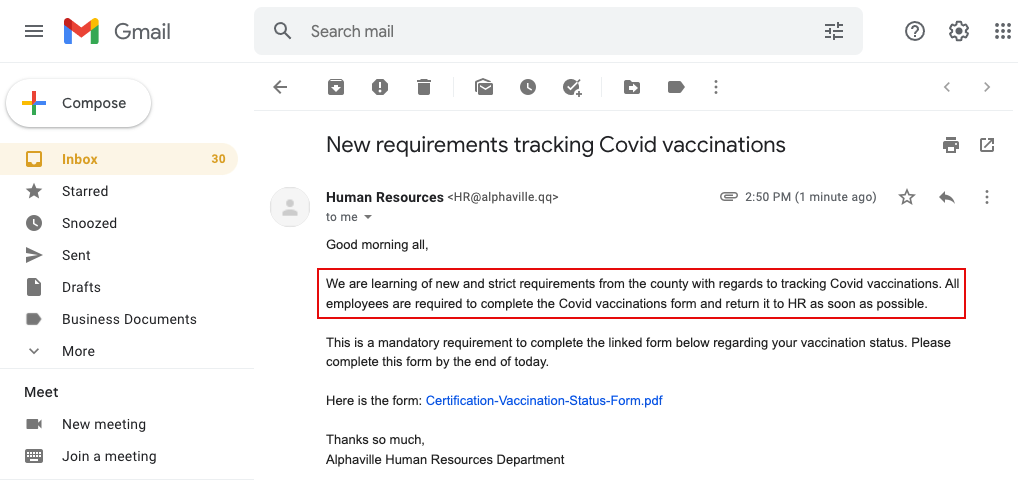
Red Flag 3: Shocking or timely content. Attackers have been more successful when their email attacks reference timely events and topics such as COVID-19.
Red Flag 4: Sense of urgency. This message is telling you to perform an action right away. The attacker hopes you don’t pause to think for a few moments and see that this is a suspicious message and should be reported to your IT team as an attack.
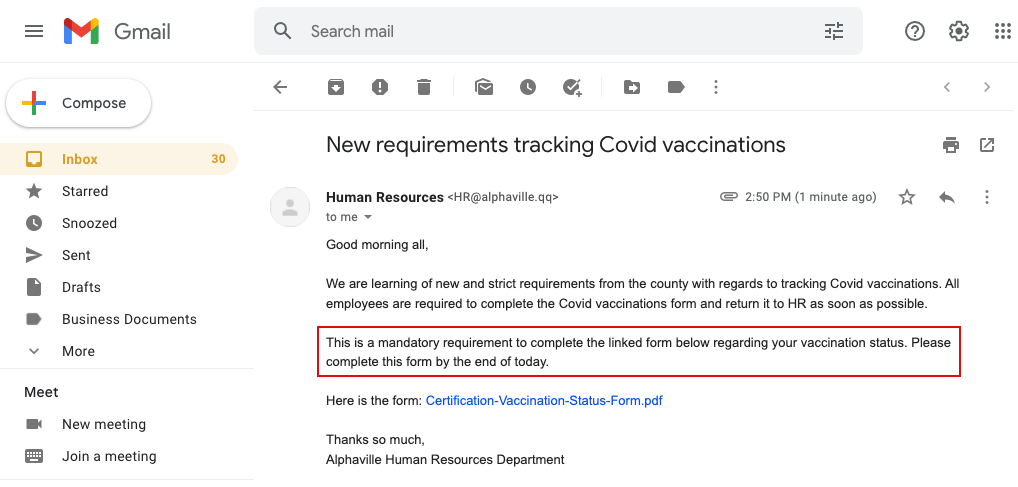
Red Flag 5: An improper link to click on. This is one of the most obvious flags of all. Hovering over this link reveals the address. If it looks off, it could be for a website that will try to steal your password or attempt to install malware on your computer. Always hover your mouse (or long press on mobile) over every link, every time, in order to determine where you will be browsing. No exceptions!
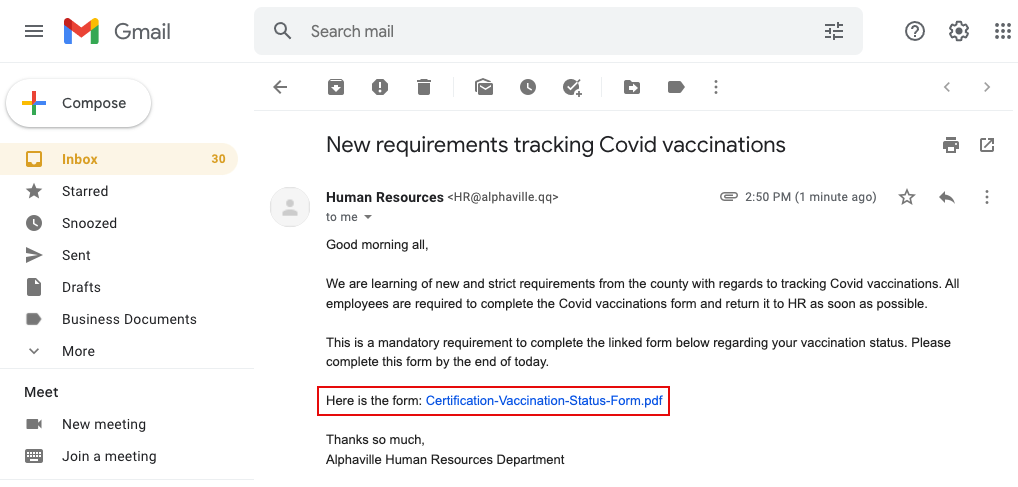
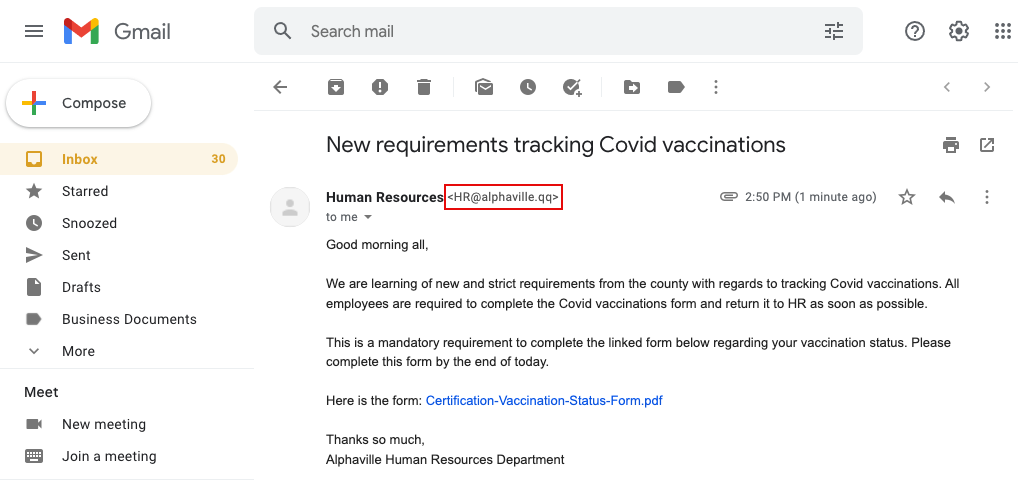
Red Flag 6: A strange email address. This should be an easy one — it’s safe to say the “qq” domain is not Alphaville’s. If the domain isn’t what it should be or is in any way suspicious, steer clear and delete.
And of course, always keep an eye out for the strange grammar and misspellings — a classic telltale sign of a scam email.
In the end, we are still fighting these security battles with email and phishing because it is still enormously effective for attackers today. Some messages can subconsciously pull at our heartstrings and emotions, which is all that needs to happen in order to get you to take an action, whether it is replying to a message, clicking a link or opening an attachment.
How do you and your colleagues stay safe when these attacks and their “red flags” keep changing? It’s as simple as 1-2-3:
- Be suspicious of every email you receive, and extra suspicious of those which concern money or other things of value.
- Hover over every link, every time before clicking.
- When in doubt, throw it out! You can also reach out by phone or instant message to the person or department that supposedly sent the email and ask if it’s legitimate.
Email attacks are not disappearing any time soon. Being able to recognize the signs of one and work safely with email every day is a critical skill everybody needs to have. Stay safe!
Want More Insight?
Each Merit Member organization gets two FREE hours of CISO consulting with our Cyber Range team to discuss additional cybersecurity strategies that can save you both time and effort. Contact our team to schedule an appointment.