The modernized electric grid, the smart grid, integrates two-way communication technologies across power generation, transmission and distribution to deliver electricity efficiently, securely and cost-effectively. Its advanced metering infrastructure (AMI), now expanding to customer premises, allows for real-time pricing and demand response schemes. However, this real-time messaging exposes the entire grid to cyber security threats ranging from attacks that disable information exchange between “smart meters” and data fusion centers to spurious payload content and “false data injection attacks” [1] that could lead to incorrect assessment of actual power demand.




Figure 1. A wireless network of ZWave sensors communicates with Raspberry Pi’s for data collection. The collected data are used as input in the anomaly detection method.
Such nefarious activities can compromise the grid stability and efficiency. Sophisticated attackers are in place of successfully launching them and, in fact, several security incidents against industrial control networks have already been documented. Known cases include the Stuxnet worm and the attacks against Iranian nuclear facilities [2], the compromise of a steel mill in Germany [3], and the cyber attacks on the Ukrainian power grid [4]. At the same time, the proliferation of Internet-of-Things (IoT) devices is introducing a plethora of network-ready elements (from smart thermostats to entertainment systems and baby monitors) into our homes. Such devices are becoming an intrinsic part of our lives due to the convenience they offer, but are enlarging the attack surface. One can imagine a malicious actor that comprises a vulnerable device, and then pivots through the home-area network to acquire access to an unsecure home smart energy meter and spoof its payload contents.
It is, hence, important to quickly and automatically detect such malicious activity. A team of researchers from Merit Research, University of Michigan and Eastern Michigan University are investigating machine learning algorithms that can automatically detect the onset of “false data injection attacks” in home-area networks [5]. Via a correlative monitoring approach, the team measures information within a home-area using inexpensive sensor nodes (e.g., motion, temperature, luminosity, etc. — see Figure 1) and correlates this information with the electricity usage reported by the smart meter. Using the collected data, the team “trains” a forecasting model that is then used to predict the electricity usage based on the independent sensor readings. Significant deviations between the actual electricity meter reading and the predicted value is an indication of a meter anomaly (Figure 2).
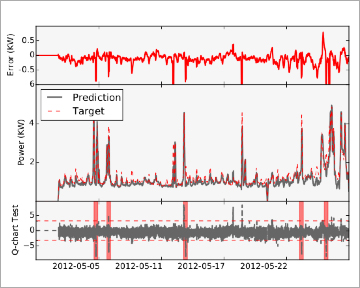
Figure 2: Prediction of electricity along with the actual meter reading (see [5] for more details).
The team has also partnered with NextEnergy in an effort to transition the algorithms and the technology into a working prototype. NextEnergy is a nonprofit organization based in Detroit, Michigan, whose mission, among others, includes the advancement, development and acceleration of energy technologies. NextEnergy has provided the research team access into the NextHome facility, a smart home with hybrid power distribution, generation and storage that plays the role of a “living lab” for showcasing new connected technologies. NextHome also performs data-driven experiments to validate emerging business models for products and services at the intersection of energy, mobility, and built environment (Figure 3). The research team has been developing a home-area monitoring solution that implements the correlative monitoring approach discussed earlier using Raspberry Pi’s and off-the-shelf Z-Wave nodes (see Figure 1), and with the support of NextEnergy the team has deployed the monitoring system into NextHome for real-world measurements and evaluation. The Raspberry Pi-based monitoring system has been in place since early 2016, and the research team is currently working on evaluating the accuracy and performance of the detection system on a variety of case studies.


Figure 3: NextEnergy’s NextHome and the research team.
Acknowledgement: this project is supported by the National Science Foundation’s Secure and Trustworthy Cyberspace program.
REFERENCES
- Yao Liu, Peng Ning, and Michael K. Reiter, “False data injection attacks against state estimation in electric power grids,” in Proceedings of CCS ’09, New York, NY, USA, 2009, CCS ’09, pp. 21–32, ACM.
- N. Falliere, L. Murch, and E. Chien, “W32.stuxnet dossier,” 2011.
- R. Lee, M. Assante, and T. Conway, “German steel mill cyber attack,” 2014.
- R. Lee, M. Assante, and T. Conway, “Analysis of the cyber attack on the ukrainian power grid,” 2016.
- M. G. Kallitsis, G. Michailidis, and S. Tout, “Correlative monitoring for detection of false data injection attacks in smart grids,” in IEEE SmartGridComm 2015, Miami, Florida, November 2015.