This report was written by Michalis Kallitsis and Abhishek Balaji Radhakrishnan.
In the last quarter of 2016 we were introduced to new types of devastating Distributed Denial of Service (DDoS) attacks, namely attacks based on vulnerable or unsecured Internet-of-Things (IoT) appliances (e.g., internet cameras, home routers, DVRs, etc.). The exploitation of such devices led to perhaps the largest DDoS attacks historically recorded. Facilitated by millions of compromised IoT devices (many devices participating in the attacks are known to be compromised by the Mirai malware [8]), assault traffic to a popular security blog [1] reached 665 gigabits-per-second (Gbps), while the hosting provider OVH experienced 1Tbps rates [2]. A third attack on Dyn’s DNS infrastructure caused severe outages to major U.S. websites, including Twitter, Paypal, Github, etc. [3, 4, 5].
In this post, we showcase evidence of the outages caused by the attack against Dyn on October 21st, 2016, as observed and captured by Merit’s DNS resolvers. Dyn, a company that offers managed DNS services [6], suffered large DDoS attacks in three phases [5]:
Phase 1 (11:15-13:40 UTC): attack affected mostly the U.S. East Coast
Phase 2 (15:55-20:40 UTC): this phase has a global impact
Phase 3 (21:25-08:10 UTC): mitigation phase, most users unaffected
Data collected from Merit’s DNS infrastructure show clear evidence of service unavailability occurring during “Phase 2” plus some minor service interruption during “Phase 1”. In particular, we checked our DNS logs for DNS return codes of type SERVFAIL [7]. The following figures illustrate that the volume of SERVFAIL responses suddenly increases at about 18:00 UTC and outages persist until about 21:00 UTC. We observed outages for several websites, including Spotify, Playstation, Twitter, PayPal, GitHub, Zillow, Yashi and Reddit.
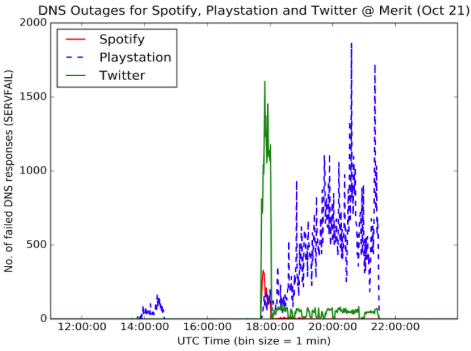
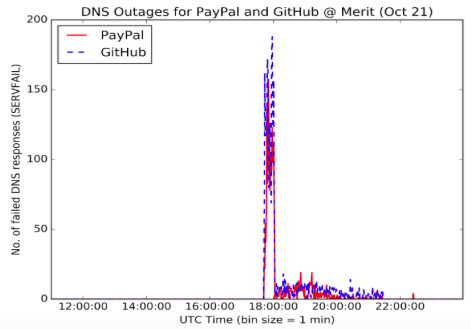
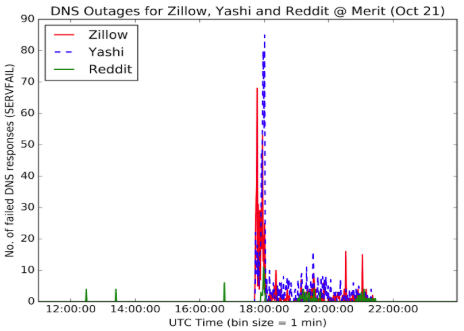
What caused the above behavior on Merit’s DNS resolvers? As we discussed, Dyn runs DNS services for many organizations, including the ones we see in the figures above. For example, typing “dig -t ns twitter.com” we get:
; <<>> DiG 9.8.3-P1 <<>> -t ns twitter.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 2358 ;; flags: qr rd ra; QUERY: 1, ANSWER: 8, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;twitter.com. IN NS ;; ANSWER SECTION: twitter.com. 13308 IN NS ns1.p34.dynect.net. twitter.com. 13308 IN NS ns2.p34.dynect.net. twitter.com. 13308 IN NS r01-01.ns.twtrdns.net. twitter.com. 13308 IN NS d01-02.ns.twtrdns.net. twitter.com. 13308 IN NS ns4.p34.dynect.net. twitter.com. 13308 IN NS ns3.p34.dynect.net. twitter.com. 13308 IN NS d01-01.ns.twtrdns.net. twitter.com. 13308 IN NS r01-02.ns.twtrdns.net.
Notice that 4 DNS servers (e.g., ns1.p34.dynect.net) are Dyn-managed servers, responsible for resolving queries for the twitter.com domain. As a result, if these servers are unavailable due to a denial of service attack, queries destined to them involving the domain twitter.com will either be served with excessive delays or not served at all. Indeed, during the second phase of the Dyn DDoS attacks, many queries issued by Merit’s DNS resolvers on behalf of several Merit customers were unable to be answered/served by Dyn’s infrastructure. As a result, Merit’s DNS resolvers would respond back to their users with SERVFAIL messages.
Unfortunately, this trend of IoT-assisted attacks is likely to continue and worsen. Many IoT nodes currently on the internet are embedded systems that remain unpatchable (by their manufacturers, e.g., because they went out of business) and/or are not well maintained by their users (something totally understandable and expected, since many users are not technology-savvy) [9]. As of this writing, Merit’s network telescope (aka Darknet) still captures significant internet scanning activities that can be attributed to the Mirai botnet foraging for new IoT devices.
References:
[1] https://krebsonsecurity.com/ 2016/09/krebsonsecurity-hit-with-record-ddos[2] http://securityaffairs.co/wordpress/51726/cyber-crime/ovh-hit-botnet-iot.html
[3] http://dyn.com/blog/dyn-statement-on-10212016-ddos-attack/
[4] https://www.nytimes.com/2016/10/22/business/internet-problems-attack.html
[5] https://blog.thousandeyes.com/dyn-dns-ddos-attack/
[6] http://dyn.com/managed-dns/
[7] http://www.ewhathow.com/2013/09/what-are-the-common-dns-return-codes-like-nxdomain/
[8] https://motherboard.vice.com/read/internet-of-things-malware-mirai-ddos
[9] https://www.schneier.com/essays/archives/2014/01/the_internet_of_thin.html